Penetration Test
Vulnerability Analysis from an Attacker's Point of View
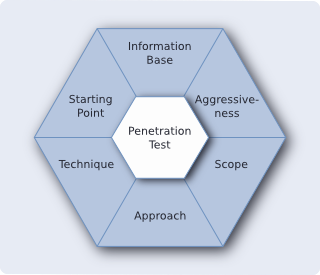
Tailor-Made Penetration Tests
IT systems that are connected to the internet or other networks and thus are accessible from the outside, are often targets of hackers who try and gain unauthorised access to your IT infrastructure. A penetration test can help you prevent such attacks from happening as it offers the possibility to test your system security from an attacker's perspective. This allows you to identify not only the technical but also the organisational and conceptual weaknesses within your company.
Depending on your specific needs we develop a test concept suitable for your organization by combining the six penetration test criteria according to your requirements. Thus, we are able to create a penetration test tailored to best suit the needs of your company. The basic procedure we follow, however, always consists of the following five phases:
1 Preparing the Penetration Test
At the beginning of the project, we work with you to define the penetration test objectives, scope, types, procedures, emergency measures, and test objects. Furthermore, we discuss with you the potential risks that the selected penetration test implies.
2 Obtaining and Evaluating Information
We gain as comprehensive and detailed an insight as possible into the systems installed in your infrastructure including potential targets. Our procedure in this phase depends on the criteria you have selected for the penetration test
3 Analysing the Risk
The next step is the evaluation of the gathered information, which serves as the basis for target selection.
4 Carrying out the Penetration Test
This is the active phase of the penetration test. Here, we actively attack the selected systems based on the results of the previous phases.
5 Analysing the Result
We present our penetration test result in the form of a detailed report including the identified weaknesses as well as recommendations on eliminating them.
And what can we do for you?
or feel free to contact us.
